Do hackers use proxy servers?
A hacker usually uses a proxy server to hide malicious activity on the network. The attacker creates a copy of the targeted web page on a proxy server and uses methods such as keyword stuffing and linking to the copied page from external sites to artificially raise its search engine ranking.
Can hackers bypass proxy servers?
Hackers are bypassing proxy servers all the time and doing so for a variety of reasons. In this SearchSecurity.com expert Q&A, Ed Skoudis points out the holes in your protective filtering tools.
Why do attackers use proxy servers?
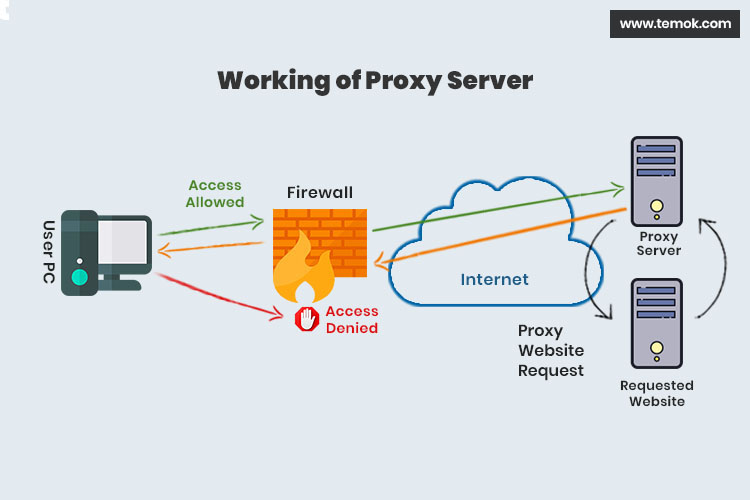
As a proxy server filters out malicious data from the internet before it reaches the company's servers, it can act as an additional layer of security. A proxy server alone might not save the company's network from all hacking attempts, but it can add to the security of the system and lower the risk of cyberattacks.
Do hackers use proxy servers to hide their identities?
Here are the various ways in which hackers hide their IPs from authorities. No matter what your level of expertise with technology, a proxy is by far the go-to to hide your information on the Internet.
Can you still be tracked with a proxy?
Therefore, a proxy server does change your IP address, but it does not provide full anonymity. Your activities can still be monitored and tracked by your ISP (Internet Service Provider) and the proxy server itself.
Do hackers use proxy servers to hide their identities?
Here are the various ways in which hackers hide their IPs from authorities. No matter what your level of expertise with technology, a proxy is by far the go-to to hide your information on the Internet.
Is proxy safer than VPN?
It's easy to find free proxy servers that will hide your IP address. But if you want to keep your browsing activity hidden from snoops, logging onto the internet through a VPN is the better choice. Again, it comes down to encryption: VPNs encrypt your data while online. Proxy servers don't.
Can a VPN stop a hacker?
How does a VPN prevent hacking? By redirecting your internet traffic to disguise your IP address, it makes it impossible to track you. And by encrypting the information you send across the internet; it stops anyone who wants to intercept your information from being able to read it.
What proxy does hackers use?
Attack proxy is a tool used by hackers to automatically scan and attack a website. They can apply common attacks and check for vulnerabilities of a site or server. Popular attack proxies are OWASP Zed Attack Proxy and Burp Suite by PortSwigger.
Why is proxy better than VPN?
A VPN and a proxy are online services that hide your IP address by rerouting your internet traffic through a remote server. But a proxy works only with a single app or service, while a VPN secures all your internet traffic and encrypts it for extra security and privacy.
What are the risks of proxy server?
One of the biggest risks of using a proxy server is that it can potentially slow down your internet connection. This is because your traffic has to travel through an additional server before it reaches its destination. In some cases, this can make websites and online services take longer to load.
Can hackers see you on VPN?
Can someone track you through a VPN? It depends on your VPN. Reliable VPN services prevent tracking altogether, even in those countries where ISPs are legally obligated to keep online activity logs. That said, sketchy and free VPN services will make it easier for you to get hacked.
How do hackers mask their IP?
There are essentially two methods you can choose from to hide your IP address. One is using a proxy server, and the other is using a virtual private network (VPN). Either one will be sufficient, but there are a few cons associated with proxy servers that make VPNs a more optimal choice for many.
How do hackers mask their identity?
Hackers will often use secure software such as a proxy server to hide their identity and funnel their communications through lots of different countries in order to evade detection. Other technologies like Tor and encryption enable them to add multiple layers to mask their identity.
Can police track you if you use VPN?
Police can't track live, encrypted VPN traffic, but if they have a court order, they can go to your ISP (Internet Service Provider) and request connection or usage logs. Since your ISP knows you're using a VPN, they can direct the police to them.
Does a VPN bypass a proxy?
A VPN can be used to bypass a proxy server or firewall and prevent your computer from being directed to a site it doesn't want to visit. This action provides an additional measure of security for anyone using a public Wi-Fi connection or any other unfamiliar network.
Can VPN Bypass proxy server?
A VPN can be used to bypass a proxy server or firewall and prevent your computer from being directed to a site it doesn't want to visit. This action provides an additional measure of security for anyone using a public Wi-Fi connection or any other unfamiliar network.
Are proxy servers secure?
In general, paid proxy services are safe to use. They provide secure anonymity for the user and are typically fast, reliable, and transparent. Make sure to check the reviews for a proxy before you begin using it; however, most paid proxy programs are authenticated and can be trusted to handle your traffic.
Is proxy really secure?
Improved security: Proxy servers provide security benefits on top of the privacy benefits. You can configure your proxy server to encrypt your web requests to keep prying eyes from reading your transactions. You can also prevent known malware sites from any access through the proxy server.
Do hackers use proxy servers to hide their identities?
Here are the various ways in which hackers hide their IPs from authorities. No matter what your level of expertise with technology, a proxy is by far the go-to to hide your information on the Internet.
Is proxy really secure?
Improved security: Proxy servers provide security benefits on top of the privacy benefits. You can configure your proxy server to encrypt your web requests to keep prying eyes from reading your transactions. You can also prevent known malware sites from any access through the proxy server.
Does a proxy change your IP?
A few different types of proxies can be used to change your IP address: HTTP/S proxies – Usually either browser extensions or special websites that work like a browser within your browser. They only change the IP address on data sent to and from your browser, but do not affect other apps or even DNS traffic.
Does antivirus stop hackers?
Antivirus software is a program designed to detect malicious threats, viruses, files, and other unauthorized software. When you download a file that can be identified as a threat, antivirus software can also help you remove it before a hacker is able to harm your system. In short, antiviruses defend us against hackers.
Can the police stop hackers?
For example, a hacker can be charged with a crime if they lack consent or any lawful authorization to enter another's computer system. They may have such authorization from a law enforcement agency and/or a court order.
What won't a VPN protect you from?
A VPN helps you stay invisible and behind the scenes, but it doesn't give you immunity against online risks like malware, ransomware, phishing attacks, or even computer viruses. That's where your antivirus software comes in.
What do most hackers use to hack?
Some of the most famous hacking tools in the market are Nmap (Network Mapper), Nessus, Nikto, Kismet, NetStumbler, Acunetix, Netsparker, and Intruder, Nmap, Metasploit, Aircrack-Ng, etc.