What can a hacker see when they hack your phone?
Hackers can also use keyloggers and other tracking software to capture your phone's keystrokes and record what you type, such as search queries, login credentials, passwords, credit card details, and other sensitive information.“Therefore, if someone hacks your phone, they would have access to the following information: email addresses and phone numbers (from your contacts list), pictures, videos, documents, and text messages.” Additionally, he warns, hackers can monitor every keystroke you type on the phone’s keyboard.
Can hackers see everything you do on your phone?
Look when a hacker has installed any malicious code of app or software in your device then they can see your phone screen,use it remotely or use it and have full access and can access everything which is linked to your device.
Can hackers see my screen?
While all operating systems have vulnerabilities, hackers find ways to exploit them and gain access to a device. Physical access. If attackers obtain physical access to your phone or computer, they can install malicious software and monitor the device's screen activity.
Can hackers see you through your phone camera?
Believe it or not, hackers can turn your mobile camera on and off, record, and sometimes even save media from your camera roll by installing spyware or remote-access Trojan malware. Pretty scary, right?
What are hackers looking for on your phone?
Things like your passwords and account numbers, emails, text messages, photos, and videos. If your phone ends up in the wrong hands, someone could steal your identity, buy stuff with your money, or hack into your email or social media accounts.
Can hackers see your camera?
Unfortunately, hackers can access this software with malware and see anything in your camera's field of vision. When they do this, it can cause the indicator light to flicker on. New files appear on your device without your knowledge: Files you don't recognize may appear harmless at first glance.
Can you remove hackers from your phone?
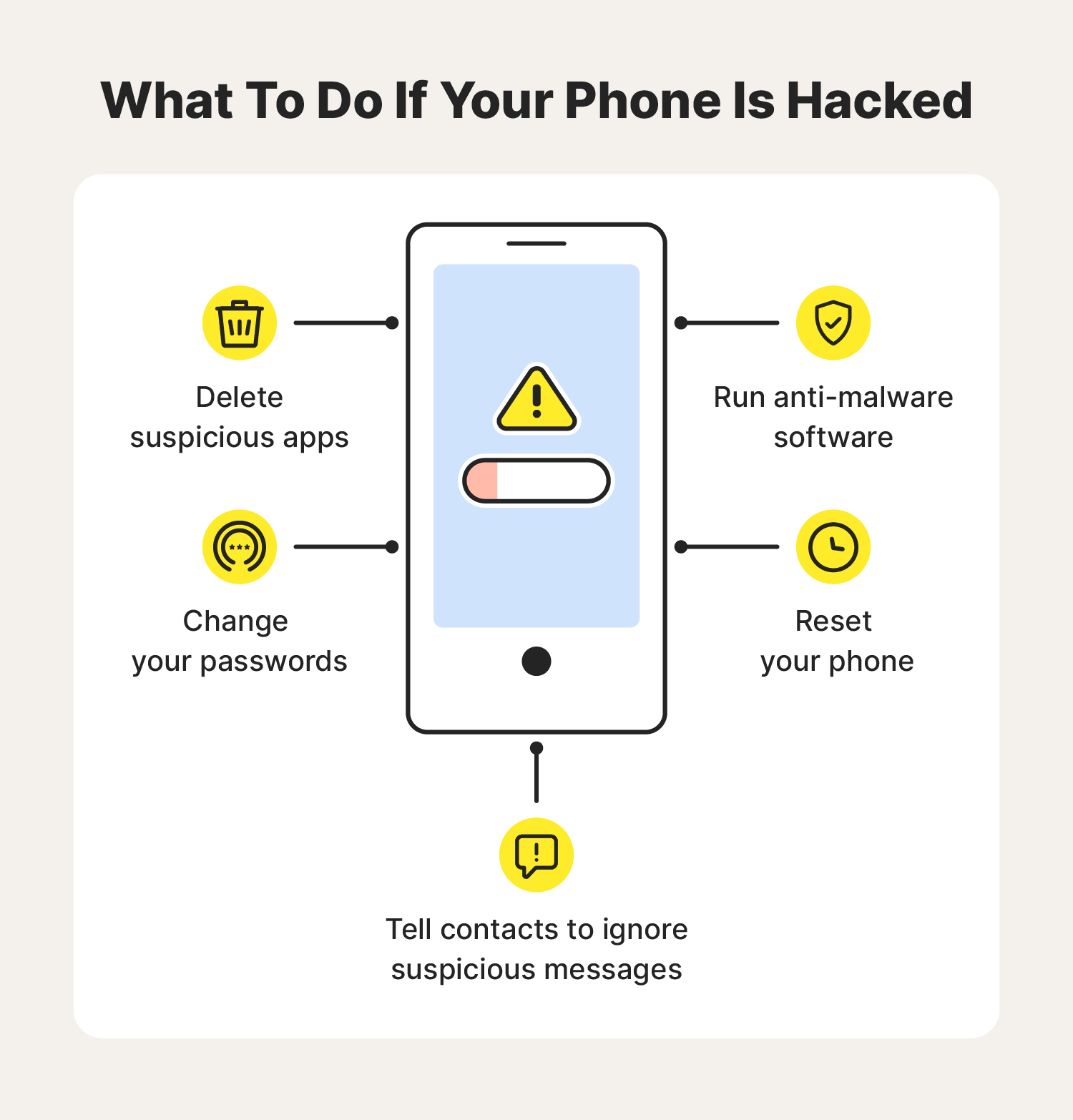
Android antivirus software locates the sneaky malware hackers use to mess with your phone and then deletes it completely. Just choose a trustworthy antivirus for your phone like VeePN Antivirus, and it will do the rest: Get VeePN for Android risk-free.
What are the 2 possible signs that you have been hacked?
Here are a few indications you've been hacked: Your email has been sending messages you didn't create. Your passwords have changed without you knowing. Your device is installing the software you didn't authorize.
How do you know if your screen is being monitored?
The best way would be to check if someone is monitoring your phone, is to download this app called Monitor Scanner . It will find any instance of spyware on your phone, as well as the person who installed it, along with their phone number and social media info. Best of all, it works with iOS and Android.
What are hackers looking for?
Many online services require users to fill in personal details such as full name, home address and credit card number. Criminals steal this data from online accounts to commit identity theft, such as using the victim's credit card or taking loans in their name.
Can I tell if my phone is being spied on?
Settings such as GPS and location functions may turn on unexpectedly or you may see random reboots. If you are suddenly using far more data than normal, this could be an indication that information is being sent from your smartphone or that remote connections are active.
How do you know if a camera is watching you?
Look for a Blinking Red Light If you can see the light from outside the camera, it means the camera is watching you. However, some cameras may have other indicators that they are actively recording instead of red light – so make sure to check your manual before assuming that no red light means the camera isn't working.
Am I being watched through my phone?
Cameras and microphones turn on randomly That means the phone is using the microphone or camera or an app. While there are many legitimate reasons your phone may be listening to you, if you notice these indicators turning on and off, it might mean that a piece of malware has tapped your phone and is recording.
Is my phone being monitored by anyone?
Here's what to do: Check phone files. It's possible to find spy software on an Android by looking at your device files. Open Android Settings > Applications > Manage Applications or Running Services and you may be able to spot suspicious-looking files.
Can anyone see you through your phone?
Whether you're using an iPhone or Android device, privacy is not a given on your smartphone. If you're concerned someone may be watching you through your phone, check for suspicious applications, unusual camera behavior, and the following signs someone is watching you through your phone.
Can hackers hack your phone without you knowing?
Phone hacking can compromise your identity and privacy without you even knowing. Fraudsters continuously evolve and improve hacking methods, making them increasingly harder to spot. This means the average user might be blind sighted by any number of cyberattacks.
Should I cover my webcam?
There aren't many legitimate security reasons for needing a cover, but experts say it can't hurt. If you worry about accidentally leaving your video camera on, a camera cover could ease your worries. Jonathan Young, associate vice president of Vantage Technology Consulting Group, uses webcam covers for this reason.
Can someone watch you through your phone without you knowing?
Spyware apps surreptitiously run on a device, most often without the device owner's awareness. They collect a range of sensitive information such as location, texts and calls, as well as audio and video. Some apps can even stream live audio and video.
Can hackers hack your phone without you knowing?
Phone hacking can compromise your identity and privacy without you even knowing. Fraudsters continuously evolve and improve hacking methods, making them increasingly harder to spot. This means the average user might be blind sighted by any number of cyberattacks.
Can I block a hacker?
A good security app can help you block hackers from your phone as well as detect any threats or vulnerabilities that may already be on there. Certo Mobile Security for iPhone and Android are trusted by millions worldwide to help protect their device's from cyber attacks.
Can a hacker freeze your phone?
If your apps are frequently quitting, or your phone is regularly freezing up, it may be because your phone was hacked and malware is hogging your phone's resources. Poor performance could also signal that you need to update your phone's software, which is essential for phone security.
Can you see if someone hacked you?
Check for suspicious logins on your accounts Check your social media, email, and other accounts for suspicious logins or devices that you don't recognize. For example, you can use Google's Activity Log to see if anyone is logged into your Gmail account and then force them to sign out.
What being hacked looks like?
If your computer is hacked, you might notice some of the following symptoms: Frequent pop-up windows, especially the ones that encourage you to visit unusual sites, or download antivirus or other software. Changes to your home page. Mass emails being sent from your email account.
Does my phone screen record?
Android 11 and later versions have built-in screen recording features that make it easy for users to record their device's screen without additional apps or tools.
Can you tell if someone is screen recording?
So, in this sense, the answer is no; websites cant detect user activities like screen capture. However, if the website has you download some software and install it, it can most probably recognize external screen capture tools being used on their web pages (if they want to).
What do hackers want the most?
Hackers love data. They want to get their hands on the email addresses, phone numbers, financial details, Social Security Numbers (SSNs), and other sensitive information stored in your system. This information may belong to your employees, customers, or business associates. Whatever you've got, hackers want it.